Managing API Keys
Keeps your environment secure: create, regenerate or delete API keys
Create an API Key
- Log in to the Tatum Dashboard.
- Go to the [API Keys] page.
- Click the [Create API key] button
Attention
- This functionality is reserved for paid plans.
- All Team Members can create API keys
Regenerate an API Key
-
Log in to the Tatum Dashboard.
-
Go to the [API Keys] page.
-
Find the auth API Key(s) you have issues with.
-
Click the [...] Menu.
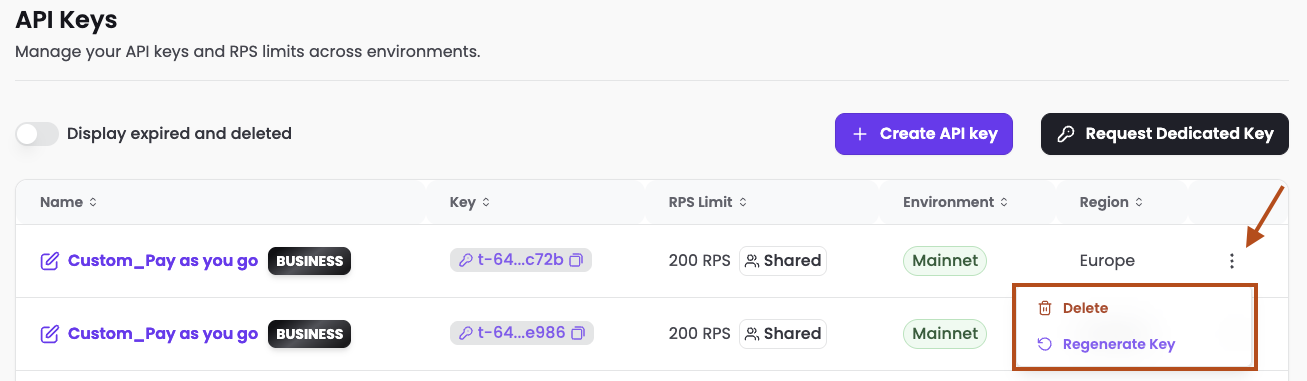
-
Click "Regenerate Key"
-
This will replace the API Key with a new one. You will need to update the key anywhere it's used.
Attention
- When regenerating an API Key, keep special attention to KMS since it requires a 1:1 match with the auth API Key that broadcasts transactions for signature.
- All Team Members can regenerate API keys
Delete an API Key - Stop it from working
-
Log in to the Tatum Dashboard.
-
Go to the [API Keys] page.
-
Find the auth API Key(s) you have issues with.
-
Click the [...] Menu.
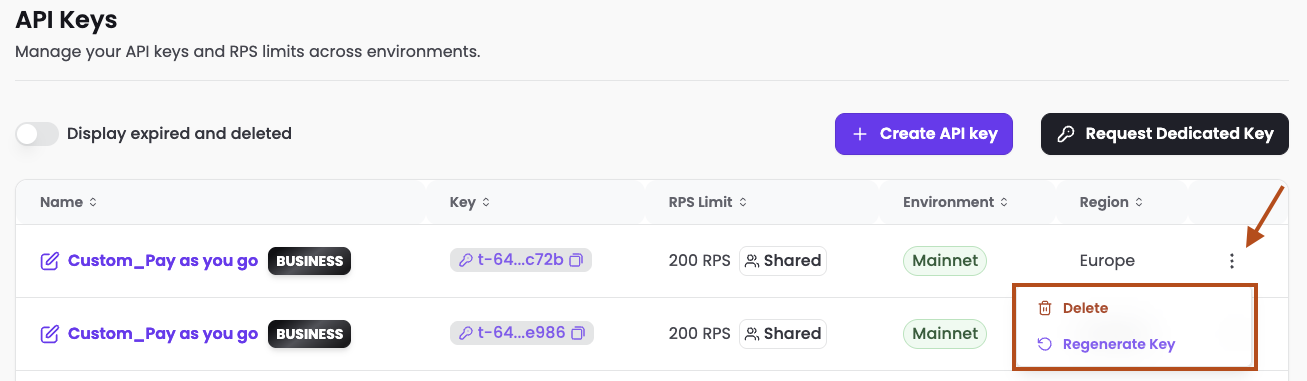
-
Click "Delete"
-
Confirm the deletion.
Warning
- All Team Members can delete API keys.
- Deleting an API key deletes all Virtual Accounts and Subscriptions to notifications. This action is irreversible.
Important Information
If you suspect or are sure that your API Keys have been compromised or exposed, you can regenerate or expire them.
Disclaimer
The auth API Keys function as the primary means of authentication for requests made through both the REST API and the Tatum SDK. They facilitate access to sensitive data and critical functionalities within users' applications. Any compromise or breach of these keys may lead to unauthorized access, data breaches, and potential financial loss.
Users are advised that by utilizing our platform and its services, they accept full responsibility for the protection and security of their auth API Keys.
Users are strongly encouraged to exercise due diligence and vigilance in managing and securing their auth API Keys to ensure the continued security of their applications and data.
WarningTatum disclaims any liability or responsibility for any unauthorised access, data breaches, or financial loss resulting from the misuse or compromise of the API Keys.
Updated 4 months ago